File encryption is a method of limiting unauthorised or undesirable access to data by encrypting/scrambling the content of files as they are written to storage such as a hard drive – or encrypting the data ‘at rest’. Generally, data encrypted with some software using an encryption key or passphrase/password can only be decrypted/converted back to its original form using the same method.
File encryption does not provide other functions like auditing, versioning or backup of data.
If you have special requirements for encryption of research data, or are unsure of the encryption requirements for your data, please contact rdm@unsw.edu.au.
Under the UNSW data handling guidelines (§5.3), any data classified as Private or above under the UNSW data classification standard should be stored encrypted at rest. This encryption should follow the UNSW IT Security Standard ITSS_21 Secure Algorithm List; file encryption/encryption of data at rest is generally symmetric encryption.
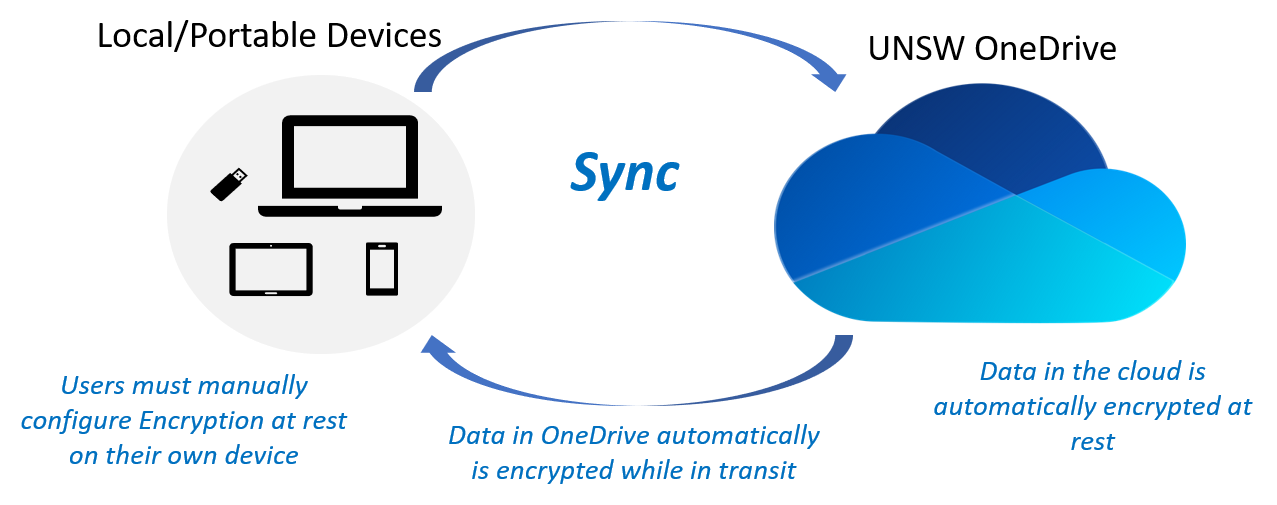
If you are storing your research data on UNSW OneDrive/Teams/Sharepoint or AARNet CloudStor, data is automatically encrypted at rest on this cloud-based storage and decrypted on demand when data is retrieved. However, any copies of the data synced or manually made from the cloud storage to a local computer or device will need to be separately encrypted at rest.
Recovery mechanism
A forgotten or lost encryption passphrase or recovery key means you will permanently lose the ability to decrypt and access the encrypted data. For UNSW IT SOE/managed devices, recovery keys for Windows BitLocker and MacOS FileVault full-disk encryption can be managed by UNSW IT. For non-SOE/managed and personal devices you should store encryption passphrases and recovery keys in a secure and accessible location or service, such as UNSW OneDrive or a password manager such as 1Password.
Operating system dependence
Some file encryption solutions and the ability to decrypt data are operating system dependent – for example, you can generally only use Windows to access a file or drive/volume that is encrypted with Windows BitLocker. Where a computer has multiple operating systems installed, data encrypted using one operating system may not be accessible from another.
Sharing/collaborating with encrypted data
Where decrypting and accessing data requires interactive entry of a passphrase/password, sharing of or collaboration using this data requires all individuals involved to securely receive and appropriately manage this passphrase. You may wish to consider a data platform such as UNSW OneDrive which automatically mediates access to encrypted data for authorised users.
Choosing a strong password
Encryption passphases or passwords should be constructed following a strong password policy such as the UNSW IT Security Standard ITSS_05 §1.8 'Password management':
- at least eight characters
- contain three of: uppercase characters, lowercase characters, numbers, punctuation/special characters
- not contain or be based on your zPass, your name, or something that can be readily guessed
Things to consider
- To automatically start your computer from a BitLocker-encrypted drive it needs a Trusted Platform Module (TPM) security chip v1.2 or later plus a Trusted Computing Group (TCG)-compliant BIOS or UEFI firmware
- BitLocker-encrypted drives/volumes can't be accessed from non-Windows operating systems such as Linux, or older versions of Windows including XP
Setting up encryption on SOE/managed devices
BitLocker drive encryption should be enabled on all SOE/UNSW IT-managed Windows computers. If yours doesn't have this, contact the UNSW IT service desk.
Setting up encryption on other devices
See this Microsoft support article. You can create and locally store a recovery key, or store it in your Microsoft account.
Things to consider
- User account passwords are also used to unlock a FileVault-encrypted disk – if a user password is compromised, this will allow for both authenticating as that user and accessing their encrypted data
- FileVault 2 (OS X 10.7 onwards) encrypts the entire startup disk; the original/legacy FileVault (OS X 10.3 onwards) only encrypts user home directories
- Some 2017–2020 Macintosh models feature the T2 security chip which separately provides for automatic encryption of data at rest on internal storage
Setting up encryption on SOE/managed devices
You will need to have Administrator access to your device to undertake this process.
- Go to the Apple Menu
- Select System Preferences
- Click on the Security & Privacy icon
- Click the FileVault tab
- Click the Lock and type your administrator password
- Click Unlock
- Click the “Turn on FileVault” button
- Select Store your recovery key at "UNSW IT MDM". Click Continue
- If you are prompted, click Restart to restart your Mac and begin the encryption process
- After your computer restarts, log in and you will see the Security & Privacy window displaying the progress of the encryption.
Setting up encryption on other devices
See this Apple support article. You can create and locally store a recovery key, or from OS X 10.10.5 onwards store this key in your iCloud account.
Linux Unified Key Setup (LUKS) is a standard for encrypted storage of partitions, full drives, file vaults and external drives on Linux systems.
Things to consider
- Converting a full drive or existing partition to LUKS encrypted storage will erase/render inaccessible all existing data in this location. You may need to make a temporary copy of data to some separate storage, then restore from this to the encrypted storage once established.
- LUKS encrypted storage is generally unlocked using a passphrase – forgetting or losing access to this will mean losing the ability to decrypt and access the data
Setting up encryption on Linux
Many Linux distributions such as Fedora and Ubuntu provide an option for full-disk encryption using LUKS as part of the installation process – this involves setting a passphrase that you need to enter when booting the machine to unlock this encrypted storage.
To convert an existing partition to LUKS encrypted storage, see this guide – note this will erase all data on the partition. You can similarly encrypt an entire disk/storage device such as an external hard drive or removable media.
You can also use LUKS to create an encrypted ‘file vault’, which you can mount and interact with but is encapsulated in a file on existing storage – see this guide.
Encrypting iPhone and iPad devices
File encryption is automatically enabled on iPhone and iPad devices when a passcode or password is set up for unlocking the device.
You should also ensure local backups of your device are password protected and encrypted. iCloud backups are automatically encrypted.
Encrypting Android devices
Android devices varies from manufacturer to manufacturer and so it is recommended that you view the manufacturer's documentation.
Before enabling encryption on your Android device, you may wish to back up your device as this process may reset the device to factory settings if encryption fails.
To enable encryption on an Android device:
- Open the Settings App
- Scroll to and tap the Security option
- Tap Encrypt Phone
- Please take note of the warnings shown after tapping this
Things to consider
- Encrypting an external drive or some removable media using a particular platform/operating system will likely tie it to that platform – for example, a drive encrypted with Windows BitLocker can't be unlocked and read on MacOS
- If you forget or lose the password/passphrase used to encrypt a device in this way, data will not be retrievable
Windows
- Insert the relevant removable media
- Select the Start Menu
- Search BitLocker
- Click Turn On BitLocker next to the relevant removable drive
- Tick “Use a password to unlock the drive”
- Make sure you create a strong password
- Select Encrypt my drive
Mac
- Open Finder
- Right click (or hold control when left clicking) on the relevant device
- Click Encrypt this drive. (If you have a SOE device and this option is not available or presents an error message, please contact the UNSW IT service desk)
- Make sure you create a strong password
Things to consider
- VeraCrypt can only have one person at a time writing to the container (additional users work in read-only)
- As VeraCrypt encapsulates an encrypted volume inside a local file, if syncing to some cloud/remote storage the entire file needs to be copied whenever any change is made inside the encrypted volume
- A 2016 security audit found a number of vulnerabilities with VeraCrypt v1.18
Setting up
- Download and install Veracrypt
- Create an encrypted volume by following VeraCrypt’s Tutorial Steps: 1 - 12
- Consider the setting to open the container in the file browser after the Veracrypt volume is mounted and uncheck "Never save history".
For general advice on encryption for research data, please contact rdm@unsw.edu.au.
Note: limitation on support for personal devices
For technical support and password recovery for SOE/managed devices, please contact the UNSW IT service desk.