Sensitive and Highly Sensitive data requires careful attention to how it is handled at all stages of a research project. Below is some information on different aspects of handling sensitive data.
Researchers can classify their data into one or more classifications according to the UNSW classification guidelines. Our guide on the RDM@UNSW website has a summary and examples of what types of data fit into each data classification.
Each data classification has different requirements for storing and handling that data. The UNSW Cyber Security Policies list out these requirements in detail. Generally, the more sensitive the data, the more careful you need to be when storing and using it.
These classifications and guidelines are UNSW-specific, there may also be other requirements from state/federal legislations, funding bodies or data providers that must be considered.
Careful data management planning is crucial before you start collecting sensitive or highly sensitive data. At UNSW, you can record you research data management plan (RDMP) on ResToolkit.
Using this system has many benefits including:
- ability to record and share your decisions regarding data for the project
- ability to address key issues around the data such as Ethics approvals, IP/Copyright ownership, storage/tools used and metadata standards applied.
- Ability to export a copy to give to a data provider, grants body or ethics committee
- Flexibility to update/edit the plan as situations change
If you plan to collect data classed High Sensitivity, you will need to give special attention to the handling of that data.
This is the phase that often has the most risk, as there are often challenges with collecting data in the field and de-identification of the data has likely not happened yet.
Here are some quick considerations for you to think about:
- Where will the data be stored when is is collected?
- For data entry and surveys, can you use a cloud-native tool like RedCap, Qualtrics, or Microsoft Forms?
- If you're a portable device (e.g. Laptop), is it physically secure, password protected, encrypted and backed up periodically?
- Can the data on the device be safely destroyed after it has been transferred to a more secure location?
Once your study or project has been completed, it is important to consider how long your data needs to be retained. On top of the UNSW recommendations, there are often legal requirements for this from journal publishers, funding bodies as well as state and federal legislations.
In general, sensitive data should only be kept for as long as is required, and then should be securely destroyed. UNSW Supported platforms have set retention periods you can see in our guide, but if you are using other platforms you must ensure your data is disposed of securely and at the appropriate time.
Working with Sensitive and Highly Sensitive data brings with it certain risks, so in some circumstances it is useful to modify your data so that it is less sensitive such as by removing or separating the more sensitive components of the data. This could reduce the data classification and the risk associated with of the data that you are working with.
The standard for identified data is data that is about "an identifiable individual, or an individual who is reasonably identifiable". For data containing such personal or other sensitive identifiers, one common way to reduce risk is De-identification. Both Data & Information Governance website and The Office of the Australian Information Commissioner provide guides and information on de-identification,
The basic steps for de-identification are:
- Removal of direct identifiers. Then:
- the removal or alteration of other information that could potentially be used to re-identify an individual, and/or
- the use of controls and safeguards in the data access environment to prevent re-identification.
You may need to keep a ‘key’ that matches your de-identified data with the identifying information, but this can often be separated from the data you work with, and even stored in a separate location to reduce the risk that it can be linked back to the rest of your data.
While working with your data, you must sure that you’re aware of all the places your data is stored and processed, and that these platforms are appropriate for your data. UNSW has a number of Supported Platforms which we have conducted a system classification to determine what classification of data they are suitable for. You should consider using one of these systems before looking for alternatives. Systems are classified by comparing technical and security features against the requirements listed in the UNSW Cyber Security Policies.
However, there will be some situations where your data may be stored in an external system:
- Giving data to a 3rd party, for example, to transcribe audio.
- Recording a meeting or interview to a device or external cloud service (e.g. Google Chat)
- Sending data to external collaborators
- Using an external High-Performance Computing (e.g. NCI) or Cloud Computing system (e.g. AWS, Google Cloud etc.)
- Working from home
- Collecting data from an online survey (e.g. Survey Monkey)
In some of the above situations, there is a UNSW supported Platform, which performs a similar function. In the event, you wish to use one of these platforms you must ensure the Platform is appropriate for your data in accordance with theUNSW Cyber Security Policies. If you require assistance to determine the classification of an external system or whether it is appropriate for use, please contact the RDM@UNSW team.
It can be hard to know exactly where your data is stored sometimes. UNSW Supported platforms have been set up so your data is always stored within New South Wales, but many similar platforms store data overseas, or may not even tell you where they store your data. This can be an issue particularly if you have requirements for keeping your data within a certain geographic area as part of an agreement, or if there could be legal implications of having your data stored overseas. UNSW Cyber Security Policies have a section with recommendations for what countries are appropriate for the various data classifications.
If you are using a device such as a PC, laptop, or server to store or collect sensitive data you should make sure that the device is as secure as possible. For UNSW supported platforms we have done this for you, but for other devices you might use there are some things you can consider:
- Device encryption is required for Highly Sensitive data, and on Windows and Mac there are now in-built options for encrypting your computer, and there are options for Linux also.
- Make sure you use strong passwords (long, containing letters, numbers and punctuation) to secure your device
- Make sure you have up to date Virus and malware protection software where possible.
- If you travel to another country with your device check whether your data should come with you. Local laws may allow officials to access your data
Having a secure password which no one can know or guess easily, is an important first step for any services you use. At UNSW, to ensure passwords remain secure, your zPass passwords require:
- a minimum length,
- a combination of different characters, numbers and symbols
- do not allow repeating previous passwords.
- You’ll also need to change your password every 6 months.
This is all to reduce the chance that an attacker could guess your password, or use “Brute Force” methods to guess a huge number of password combinations to break into your account. You should consider applying similar requirements for other passwords you use.
For further information, you may want to read the password advice given by The Australian Government Cyber Security Centre.
When you have sensitive data it is even more important to have a strong password, as the impact of a data breach is much greater. Having Multi-factor authentication (see below) helps a lot here, but a strong password will help protect your account either way.
Many secure systems, email services, and other services (e.g. MyGov, banking) now support or require Multi-factor Authentication (MFA). This is where, in order to login to the system, you are required to provide something you ‘know’ (a password) plus something you ‘have’ (a special code via an sms or phone app) and maybe even something you ‘are’ (fingerprint, face recognition etc). Set up correctly, this can add extra layer of security to the service, because someone who guesses or steals your password will often not have the additional information needed to log in.
UNSW's Office 365 (Outlook, OneDrive, etc) is one service where you can enable MFA to add this extra security. Contact IT to set this up on your Office 365 account. After it is enabled you maybe be prompted to configure an Authenticator app on your phone which will provide the extra code you need to log in. This code will need to be entered once every 6 months per device you use Office 365 on (laptop, phone, etc), or whenever you change your password. Enabling MFA is a requirement if you are storing Highly Sensitive data in OneDrive.
Often you will be required to share your data with other collaborators or organisations. If your data is sensitive you need to pay careful attention to how you share your data, who you are sharing it with, and how long you ware sharing the data for. ANDS (now part of the Australian Research Data Commons) have a guide on sharing sensitive data, focusing on publishing sensitive data.
Some key points are:
- De-identifying your data before sharing reduces the risk
- Check for restrictions on sharing in existing Ethics and data agreements
- You can set conditions on publishing your data
If you want to share data with collaborators, it’s important you:
- use a platform that is appropriate for the data,
- share to the right people,
- share in a secure way
For example, If you use OneDrive, you are presented with the following options whenever you choose to share a file or folder:
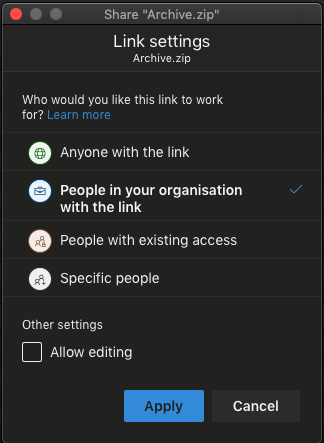
- Sharing to "Anyone with the link" is not recommended as once you have sent the link to someone, you have no further control who will gain access to the link (e.g. forwarded emails)
- Sharing to "People in your organisation with the link" is not recommended as it is essentially the same as 1
- Sharing to “specific people” is the best option as it allows you to choose specifically who will have access to the file. If you want your data to remain untouched, you can also consider disabling editing.
There are certain external platforms that are designed for sharing secure data, such as SURE, ERICA, and SeRP. Some data providers may require the use of one of these platforms in order to get access to their data.
However, technical options like these can only go so far in protecting your data. In addition, you should consider restrictions such as legal agreements, policies and procedures are in place prior to the start of a project as additional layers of security.
If you require more assistance with managing your data please contact us at rdm@unsw.edu.au